Report Suspicious Email with PhishAlarm
PhishAlarm is a new method of reporting suspicious messages directly to the IT Security Office from your Microsoft Outlook or Gmail client with the tap of a button.
This article applies to: Faculty , IT Professionals , Security & Policy , Staff , Students
For years, Cornell community members have continually helped strengthen the layers of security protecting the university's digital resources by forwarding suspicious email messages to the IT Security Office. To make it even easier for customers to notify us of potential threats, we are introducing PhishAlarm, a new button added to Microsoft Outlook and Gmail email clients.
Why Use PhishAlarm
PhishAlarm includes all your email message details
The data forwarded by PhishAlarm includes the full message, the headers of the message, and any attachments. These details can be used by the IT Security Office to track an individual email, detailing the path a message takes as it crosses mail servers.
Because PhishAlarm already provides the pertinent details, it is safe to delete the message if it remains in your inbox.
PhishAlarm reduces email replies from the IT Security Office
The IT Security Office appreciates Cornellians' diligence in reporting these messages. To respect your time, we will not email you a reply unless we want to suggest additional protective steps.
How to Use PhishAlarm
PhishAlarm lets you report suspicious emails to the IT Security Office with three quick clicks.
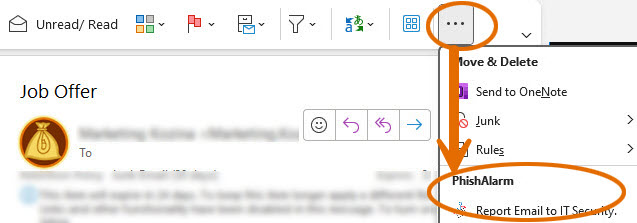
- Select the suspicious message in your email client, then click the PhishAlarm icon.
- In the pop-up box, click the blue button labeled Report Email to IT Security to confirm.
- In the next popup box, click Close to send the message to your junk folder.
- If your client does not automatically remove the message from your inbox, delete it manually after reporting as phish.
- If you accidentally select a legitimate message to report as phish, choose Cancel in step 2.
Currently, PhishAlarm appears in Microsoft Outlook desktop, web, and mobile interfaces and in the Gmail web interface. Use of the PhishAlarm button is optional, but encouraged by the IT Security Office. Customers who prefer not to use PhishAlarm and those on an unsupported email client can still manually report suspicious emails to the IT Security Office by forwarding them to itsecurity@cornell.edu.
Where to Find PhishAlarm
Look for the icon of a white envelope on a blue fish hook or the phrase Report Email to IT Security.
Depending on the client, PhishAlarm may be found in a new section on the Outlook ribbon, the side tool bars, or under More Options represented by a waffle, grid, or three dots.
Phish Reporting Improves Digital Security
Thanks to the thousands of phishing reports by Cornellians over the last 7-10 years, the IT Security Office has been able to block or mitigate serious intrusion attempts that could have compromised Cornell individuals and resources.
Using PhishAlarm data, the IT Security Office can compare local reports with national and global threat assessments streamed in real-time by our vendor, Proofpoint. This aggregated data provides a faster ranking of the phishing message or campaign in terms of its likely level of danger.
If you have further questions, please email them to itsecurity@cornell.edu.



Comments?
To share feedback about this page or request support, log in with your NetID